IIS - This implementation is not part of the Windows Platform FIPS validated cryptographic algorithms
Have you ever got the "This implementation is not part of the Windows Platform FIPS validated cryptographic algorithms." exception while trying to use some of the classes in the "System.Security.Cryptography" namespace?The exception normally thrown is a "TargetInvocationException" exception and the message that accompanies it is usually the unhelpful "Exception has been thrown by the target of an invocation". It is only when you drill down into the InnerException that you see the "This implementation is not part of the Windows Platform FIPS validated cryptographic algorithms." message. The reason that this exception is thrown is that you have tried to use a cryptographic algorithm that is not FIPS compliant.
What is FIPS compliance? FIPS stands for Federal Information Processing Standards. (link to more information) and are US Government standards that provide a benchmark for implementing cryptographic software.
WindowsXP and later operating systems have both FIPS compliant and non-compliant algorithms that can be used by developers. FIPS compliant algorithms are those that have been validated by the FIPS 140 program. One can call both the compliant and non-compliant algorithms as the check for FIPS compliance is by default turned off.
How do you turn on and off FIPS compliance checking:
Two methods:
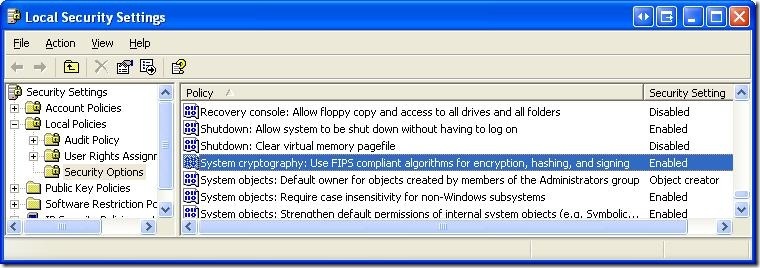
1. Go to Control Panel -> Administrative Tools -> Local Security Policy
Enable the setting for "System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing"
2. Another method is to directly edit the registry by setting the following value to 0 (disable) or 1 (enable)
HKLM\System\CurrentControlSet\Control\Lsa\FIPSAlgorithmPolicyAlternatively you can copy the following lines into a registry script file (.reg) and run it.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa]
"fipsalgorithmpolicy"=dword:00000001
Note:
One thing that I am not certain off is that this option might be
available only on Windows XP Professional OSs and not in the basic
Windows XP OS. I havent been able to confirm this via documentation -
but the option is not available on my home machine (Windows XP), but is
available on my work machine (Windows XP Pro).For Developers:
So what does this mean for developers? If you ever envision your software running on a government computer (especially in the US), you should turn on FIPS compliance checking. This way, your application that uses cryptography algorithms provided by the OS will work on all machines and you wont have to deal with the "Exception has been thrown by the target of an invocation".
For .NET Developers:
FIPS compliance checking (if turned on in the local security policy) I think was introduced starting in version 2.0 of .NET. Unfortunately, the MSDN documentation on FIPS compliance is pretty skimpy and there is no list of the algorithms in the "System.Security.Cryptography" namespace that are FIPS compliant. (Also there is no property that can be checked or an interface or base class that FIPS compliant algorithms implement - which would allow for runtime checking - hint, hint MS).
So here is a quick list that I obtained by using reflection (C# code is below)
FIPS compliant Algorithms:
Hash algorithms
HMACSHA1Symmetric algorithms (use the same key for encryption and decryption)
MACTripleDES
SHA1CryptoServiceProvider
DESCryptoServiceProviderAsymmetric algorithms (use a public key for encryption and a private key for decryption)
TripleDESCryptoServiceProvider
DSACryptoServiceProviderAlgorithms that are not FIPS compliant
RSACryptoServiceProvider
HMACMD5
HMACRIPEMD160
HMACSHA256
HMACSHA384
HMACSHA512
MD5CryptoServiceProvider
RC2CryptoServiceProvider
RijndaelManaged
RIPEMD160Managed
SHA1Managed
Does not work
ReplyDelete